Overview—The Massachusetts Regulations May Affect Your Business
In response to the growing number of data and identity theft incidents involving residents of the Commonwealth in recent years, Massachusetts regulators took significant steps toward increasing regulatory control over data security. Effective March 1, 2010, the Massachusetts Office of Consumer Affairs and Business Regulation (OCABR) adopted 201 CMR 17.00 et seq. (the “Regulation”), which is intended to establish the “minimum standards to be met in connection with the safeguarding of personal information” with the objective of ensuring the “security and confidentiality of customer information in a manner fully consistent with industry practice.”
The Regulation is comprehensive in substantive scope and in geographic reach, and applies to any entity—no matter where located—that “owns or licenses”
http://www.mass.gov/Eoca/docs/idtheft/sec_plan_smallbiz_guide.pdf
Background
Some clues may lie in the history behind the adoption of the Regulation. In 2007, the Massachusetts legislature enacted Mass. Gen. Laws ch. 93H: Security Breaches, which, among other things, mandates the reporting of data breaches involving personal information and the disposal of personal information.
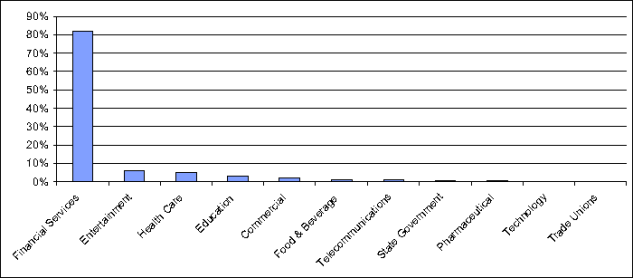
OCABR analyzed the breach notifications it received under the new law, and released two reports, on Feb. 2, 2009 and Nov. 4, 2009 (the “OCABR Reports”). The OCABR Reports indicated that over 800 breach notifications were filed with the OCABR between October 2007 and November 2009; we understand that the frequency of breaches has increased since then. Of those notifications, approximately 750 were reported by businesses, approximately 40 were reported by educational institutions and 45 were reported by state government.
OCABR also issued its first iteration of the Regulation on November 14, 2008, which was promulgated as an “emergency regulation” and originally scheduled to be effective January 1, 2009.
Not surprisingly, the Regulation focuses in large part on the sources of data breaches identified in the OCABR Reports. More to the point, those industries which have experienced large numbers of breaches—e.g., the financial services industry and retail industries—may be particularly prone to heightened regulatory and enforcement scrutiny.
Written Information Security Program
Under the Regulation, all persons who own or license personal information about a Massachusetts resident must develop, implement, and maintain a comprehensive written information security program (WISP). The requirements may have different meanings and effects on different organizations given the risk-based approach, thus each requirement should be tailored to your organization’s needs.
A look at some of the requirements and a practical analysis for each:
- Designate one or more employees to maintain the WISP. Determine who in your organization should be the point person to lead and coordinate your compliance efforts. A larger organization may wish to designate a team to be responsible for ongoing compliance, which can and should include representatives from various departments, including information technology, human resources, legal, corporate communications, audit and key business divisions. A smaller organization, or even sole practitioner, can probably manage with a single point person coordinating the various aspects of such departments as applicable. It is important to keep in mind the goal of a unified WISP that is appropriate for your organization given the type of industry, the amount of data collected, stored and transmitted.
- Identify and assess reasonably foreseeable internal and external risks: data mapping. Knowing how much personal information is owned and stored, as well as where it is maintained and how it is transmitted, will impact the extent of procedures your organization must follow. Although the Regulation does not require an organization to create a written inventory of its paper or electronic records or to post its WISP publicly, your organization should perform an internal risk assessment and analysis of the personal information it owns, stores, maintains and transmits in order to properly handle and protect that personal information in accordance with the Regulation.
13 See Frequently Asked Questions, at 4. 14 See e.g. Mary Beth Hamilton, Defining Data Mapping and Data Loss Prevention Technology for Financial Firms, Hedge IT Blog, May 6, 2010, http://www.eci.com/blog/13-defining-data-mapping-and-data-loss-prevention; David Wetmore and Scott Clary, To Map or Not to Map: Strategies for Classifying Sources of ESI, Information Management, September/October 2009, at 33.
- Develop security policies and training for employees. Each organization should have policies in place relating to the storage, access and transportation of records containing personal information both inside and outside of business premises. A policy for a smaller organization that does not store any personal information besides employee data can be as simple as locking all files in storage cabinets, locking the storage room and permitting access only to those who require it for official duties.
15 See Frequently Asked Questions, at 4.
Each organization should develop a process that prevents terminated employees from accessing records containing personal information, such as disabling access cards, usernames and passwords, and requiring the return of all company-owned equipment. Any process must be coordinated with your organization’s information technology department (if applicable) and operations and/or security departments. We recommend incorporating this process and return of equipment as part of an exit interview process.
What is most important for all organizations, is the education and training of its employees. There is no “bright line” rule as to the amount of employee training required under the Regulation—OCABR merely suggests that an organization conduct “enough training to ensure that the employees who will have access to personal information know what their obligations are regarding the protection of that information.”16 Id.
- Oversee third-party service providers. Organizations are required to (1) take “reasonable steps to select and retain third-party service providers that are capable of maintaining appropriate security measures to protect such personal information consistent with these regulations and any applicable federal regulations,” and (2) require third-party service providers by contract to “implement and maintain such appropriate security measures for personal information.”
17 201 CMR 17.03(f). We note that there is a carve-out for contracts entered into prior to March 1, 2010, which will be deemed to satisfy the Regulation’s provisions regarding third-party service providers until March 1, 2012. This exception applies even if the contract does not include any provisions requiring the third-party service provider to maintain appropriate security measures. New service provider contracts, as well as any grandfathered contracts that extend past March 1, 2012, however, must require by contract that the third-party provider will implement and maintain such appropriate security measures for personal information.
- Remedies provisions in the event the third-party provider breaches its security obligations (i.e., liquidated damages and indemnification obligations, including attorney’s fees and any costs associated with any loss of personal information by the third-party provider);
- 2. Adequate level of insurance provisions; and
- 3. Notice provisions that requires the third-party provider to notify you in the event of a suspected or known security breach, whether or not directly involving your organization.
- These contractual provisions may help ensure that the third-party service provider is aware of and agreeing to its obligations under the Regulation. Such provisions can also provide your organization with some comfort that while you cannot constantly monitor the service provider’s activities to ensure compliance, the service provider is contractually obligated to comply with the Regulation.
- Regular monitoring. The Regulation requires “[r]egular monitoring to ensure that the comprehensive security program is operating in a manner reasonably calculated to prevent unauthorized access to or unauthorized use of personal information,” and “ongoing employee (including temporary contract employee) training.”
18 201 CMR 17.03. 19 See Frequently Asked Questions, at 1, 3.
- Establish and maintain up-to-date computer security systems. To the extent personal information is electronically-stored or transmitted by your organization, the WISP must also include the establishment and maintenance of security system covering your computers, including any wireless system and encryption methods.
20 201 CMR 17.04.
- “Reasonably up-to-date” firewall protection and operating system security patches for files containing personal information on a system that is connected to the Internet and versions of system security agent software, which must include malware protection and “reasonably up-to-date” patches and virus definitions;
- 2. Secure user authentication protocols including (i) control of user IDs, (ii) “reasonably secure” methods of assigning and selecting passwords, or use of unique identifier technologies, such as biometrics or token devices, (iii) control of data security passwords, (iv) restricting access to active user and user accounts, and (v) blocking access to user identification after multiple unsuccessful attempts to gain access or the limitation placed on access for the particular system; and
- 3. Encryption of all transmitted records and files containing personal information that will travel across public networks and encryption of all data containing personal information to be transmitted wirelessly.
21 201 CMR 17.04; See also Frequently Asked Questions, at 2.
- According to the OCABR, a security requirement is considered “technically feasible” “if there is a reasonable means through technology for an organization to accomplish a required result.”
22 201 CMR 17.04; See also Frequently Asked Questions, at 2. 23 See Frequently Asked Questions, at 2.
- Encryption decrypted. One of the requirements that has raised many practical questions with organizations is the duty to encrypt certain types of data transmissions and storage devices. The Regulation requires an organization to encrypt personal information (1) traveling across “public networks” or “transmitted wirelessly,” or (2) stored on “laptops and other portable devices.”
24 201 CMR 17.04.; See also Frequently Asked Questions, at 2. 25 201 CMR 17.02; See also Frequently Asked Questions, at 3.
To the extent that encryption is not “technically feasible,” your organization must take alternative and appropriate steps to secure and protect the personal information.26 201 CMR 17.04; See also Frequently Asked Questions, at 2.
- Uploading the data to a secure website or datasite that requires the recipient to log in with a username and password to access the data;
- 2. Employing a mandatory transport layer security (TLS) link, which provides security for e-mail communication; or
- 3. Utilizing a virtual private network (VPN) link, which can be used to encrypt all types of Internet communication between organizations. We recommend working with your information technology department (if your organization has one) to understand what encryption technology is available to your organization and any alternative means available, to the extent encryption is not “technically feasible.”
- If your organization needs to send data that contains personal information to another organization that cannot receive encrypted data, such as certain governmental agencies, you should contact the recipient to set up an alternative means of transmission. And, for certain regulated entities such as broker-dealers that are required to review and monitor employee e-mails in accordance with industry-specific regulations, if mass encryption interferes with that obligation, that entity should discuss with their information technology group an alternative means by which the requisite sampling of e-mails can be reviewed.
- It is important to educate all members of your organization, which can and should be done in conjunction with your employee training, regarding the encryption requirement so that each employee understands that e-mails should not be sent outside of your organization that contain personal information without being encrypted. If an e-mail cannot be encrypted, one of the alternative methods (or other similar methods that your organization may utilize) should be utilized.
- Backup Tapes. If your organization maintains backup tapes, tapes created after March 1, 2010 must be encrypted as they are being created, but tapes created prior to March 1, 2010 need not be encrypted unless they will be transported from current storage elsewhere.
27 Id. 28 Id. While OCABR suggests utilizing secure transport such as armored vehicles and guards, Frequently Asked Questions, at 2, OCABR staff has informally noted that other reasonable means of curing transport may also suffice.
Pay Attention to Industry Standards and Other Data Security Regimes
The Regulation specifically states that its objectives are to ensure the security and confidentiality of customer information in a manner “fully consistent with industry standards,” and that the safeguards contained in a WISP “must be consistent with the safeguards for protection of personal information and information of a similar character set forth in any state or federal regulations.”
Conclusion
The Regulation requires companies to take a variety of measures to protect and safeguard personal information of Massachusetts residents. Given the nuances of the Regulation, to the extent your organization still has questions as to the practical implications of the Regulation, you should contact your attorney or a member of Bingham’s Privacy and Security Group to ensure your organization is fully compliant.
Learn more about Bloomberg Law or Log In to keep reading:
See Breaking News in Context
Bloomberg Law provides trusted coverage of current events enhanced with legal analysis.
Already a subscriber?
Log in to keep reading or access research tools and resources.