Part 1: Introduction
The use of social media in the workplace is growing at a rapid pace. Savvy businesses are using blogs, social networks, video on demand (VoD), wikis and other vehicles to quickly share information with their target audiences. The result can be greater brand awareness and an enhanced image in the marketplace. Social media can also play an important role in gathering intelligence directly from an organization’s target audience to help improve products, services and other areas of their business. As social media technology and the security for these tools continue to evolve, we imagine organizations will realize even more benefits.
Along with these benefits have come risks. ISACA has identified the following as the top five risks of social media: viruses/malware, brand hijacking, lack of control over content, unrealistic customer expectations of “internet-speed” service and non-compliance with record management regulations.
Ponemon Institute is pleased to present the findings of our study, Global Survey on Social Media Risks. Sponsored by Websense, we believe this is the first study conducted to determine what IT and IT security practitioners throughout the world think about security risks associated with employees’ use of social media tools.
As the study reveals, social media is now considered important for an organization’s ability to achieve its business objectives. Our purpose is to understand the magnitude of the risk and what actions might be taken to prevent attacks on systems and still allow businesses to integrate the use of social media into their business strategies.
The study surveyed 4,640 IT and IT security practitioners in Australia, Brazil, Canada, France, Germany, Hong Kong, India, Italy, Mexico, Singapore, the United Kingdom, and the United States with an average of 10 years experience in the field. Fifty-four percent hold positions of supervisor or above and 42 percent are employed by organizations with a headcount of more than 5,000.
In this study we asked IT and IT security practitioners in these countries about the following issues:
- the importance of social media in meeting business goals today;
- the existence of enforceable policies governing the use of social media tools in the workplace;
- the security risks created by employee usage of social media tools; and
- the use of enabling security technologies to reduce or mitigate social media risks.
We believe the following are the most salient findings from this study:
- Most respondents agree that the use of social media in the workplace is important to achieving business objectives. However, they also believe these tools put their organizations at risk and they do not have the necessary security controls and enforceable policies to address the risk.
- Organizations are most concerned with employees downloading apps or widgets from social media sites, posting uncensored content and uncensored blog entries.
- Employees are using social media tools more often for non-business purposes than business purposes.
- Malware infections are increasing as a result of social media use. Technologies considered by respondents to be most important to reducing or mitigating social media threats are antivirus/anti-malware, secure web gateway (SWG) and identity and access management.
- Organizations are increasing their internet bandwidth to accommodate the increased use of social media in the workplace.
Part 2. Analysis of key findings
In this section, we examine the impact social media is having on organizations and how organizations are responding to the risks we described previously.
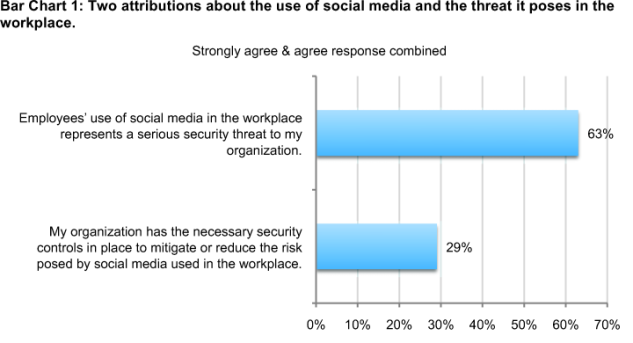
The rapid proliferation in the use of social media may have caught many organizations off guard. As shown in Bar Chart 1, most respondents (63 percent) agree that employees’ use of social media puts their organizations’ security at risk. In contrast, only 29 percent say they have the necessary security controls in place to mitigate or reduce the risk posed by social media used in the workforce.
According to Websense, potential threats exist because social circles provide a trusted attack position for cybercrime between friends when account credentials are compromised. Lures and dynamic web links can quickly infect friends and then infect their social circles. The other aspect of social media is providing cybercrime user profile information for spear-phishing and customized lures individuals are more likely to accept.
If there is a policy to address the acceptable use of social media in the workplace, 65 percent say their organizations do not enforce it or they are unsure. The top three reasons for not enforcing these policies are lack of governance and oversight (44 percent), other security issues are a priority (43 percent) and insufficient resources to monitor compliance with the policy (41 percent).
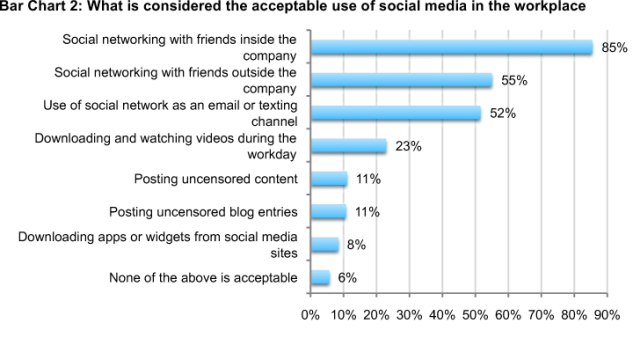
Organizations say the use of social networking with friends inside and outside the organization is acceptable. Based on this response, we believe organizations consider social media a positive tool for encouraging collaboration and building internal relationships. However, the blending of the social and work environment does create risk because devices the organization does not own are on the network and the exchange of content among employees cannot be controlled.
Bar Chart 2 reveals that 85 percent of respondents say social networking with friends inside the company is acceptable and 55 percent find social networking outside the company to communicate with friends acceptable. However, a much smaller percentage (11 percent) of respondents say posting uncensored content or blog entries on the network is acceptable and 8 percent say downloading apps or widgets from social media sites is not acceptable.
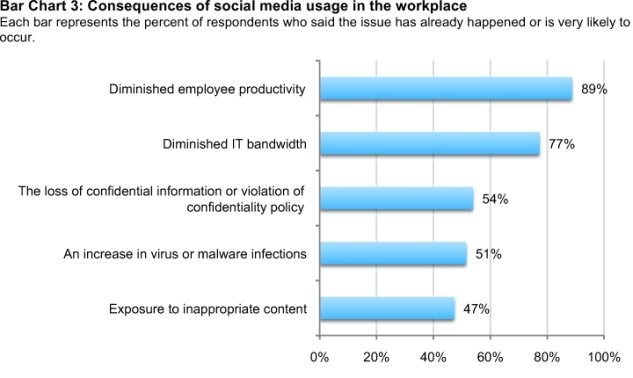
Organizations believe productivity has declined and IT bandwidth has been diminished as a result of social media usage. The top two negative consequences of an increase in social media in the workplace are shown in Bar Chart 3. These are: diminished productivity (89 percent) and diminished IT bandwidth (77 percent). Less than half (47 percent) believes exposure to inappropriate content is a negative consequence. Fifty-nine percent of organizations in the study increased their internet bandwidth (pipe) to accommodate employees’ use of social media during the past 12 months.
A reason for the need to increase bandwidth, according to Websense, is that social media includes video-on-demand (VoD) and live streaming events that will drive up bandwidth consumption. These viral videos and images gaining quick popularity from social circles between friends also make excellent lures for web threats. The web also has been a productivity concern for management since inception. However, with quotas and bandwidth controls employees can have access within reasonable boundaries keeping productivity at desirable levels.
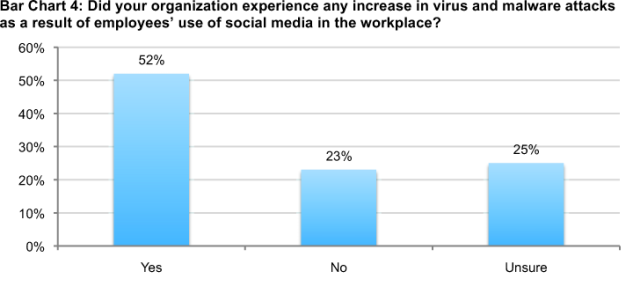
Virus and malware attacks have increased because of social media usage. Bar Chart 4 shows that 52 percent of organizations experienced an increase in malware attacks as a result of employees’ use of social media and 27 percent say these attacks increased more than 51 percent.
Social media is more often used for personal reasons. Employees are using social media for both business and non-business purposes. However, they are using it more often for personal reasons. About half (47 percent) use social media more than one-third of the time (37 percent) for business, however 63 percent use social media for non-business purposes more than one-third of the time (37 percent).
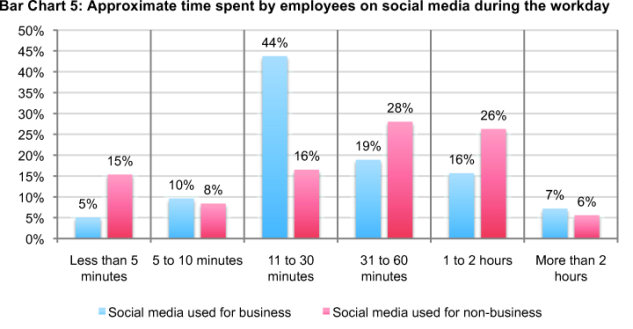
Time spent on social media for business and non-business purposes also varies, as shown in Bar Chart 5. Fifty-nine percent use social media no more than 30 minutes per day for business reasons. However, 60 percent of employees are estimated to use social media for personal reasons at least 30 minutes per day.
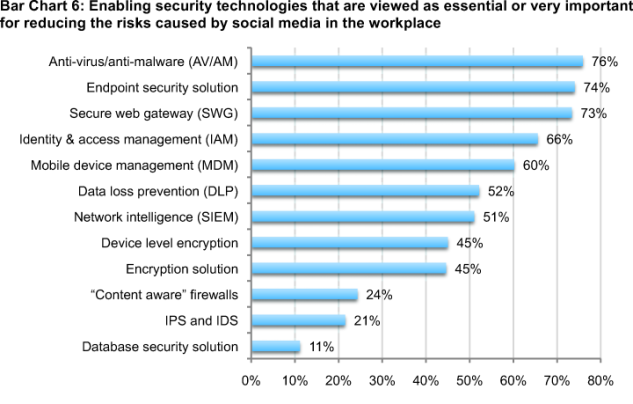
To mitigate the risks created by social media certain technologies are preferred. Bar Chart 6 shows the technologies that respondents consider most important to reducing or mitigating social media threats are anti-virus/anti-malware, endpoint security solutions and secure web gateway.
According to Websense, the dynamic social web requires an IT security defense that goes beyond signature and fixed-policy web technologies (like anti-virus and firewalls). New technologies such as social media, cloud services and mobility require real-time content security, which analyzes information in real-time as it is created and consumed. Further, Websense says that traditional defenses such as anti-virus do not provide appropriate threat protection.
Part 3. Most significant country differences
In this section, we provide an analysis of the different perceptions among IT and IT security practitioners in 12 countries concerning the use of social media in their organizations.
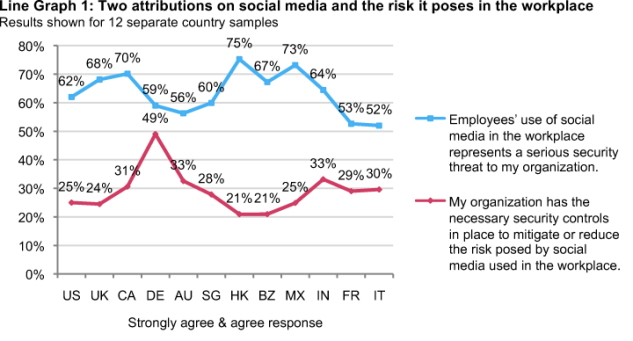
Perception of risk. As shown in Line Graph 1, countries with organizations that are most likely to see social media as a serious threat to their organization: Canada, Hong Kong and Mexico. Countries least likely to see social media as a threat are France and Italy. The country with organizations that have the most confidence in their ability to address the threat is Germany.
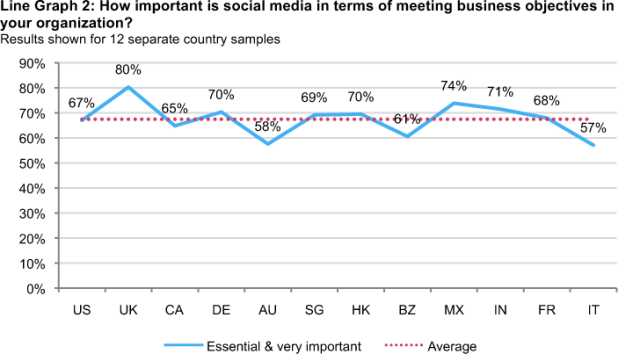
Social media as an important tool for business. The countries with organizations that are most likely to see social media as important to meeting business objectives are the United Kingdom, Mexico, India, Germany and Hong Kong (Line Graph 2). The countries with organizations that are less likely to see the importance of social media are Italy, Australia and Brazil.
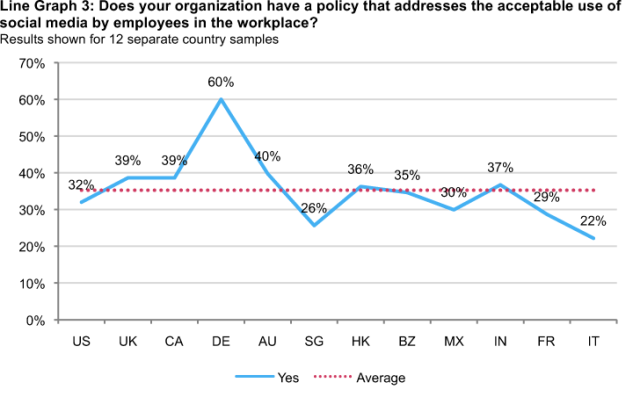
Policies to address social media usage. Line Graph 3 reveals that Germany is the only country with the most organizations that believe they have a policy that addresses the acceptable or unacceptable use of social media. Countries with organizations that are more likely to believe they are lacking such a policy are Italy, Singapore, and France.
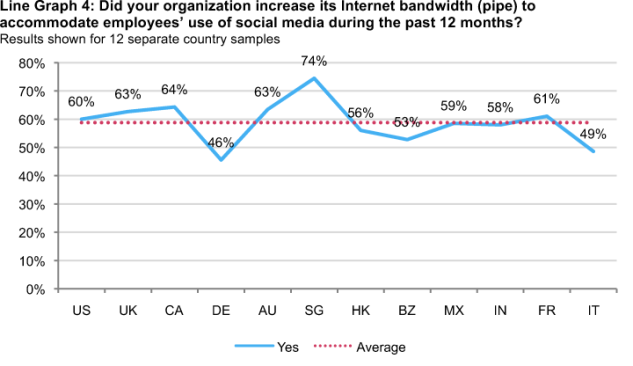
Increased internet bandwidth to support social media usage. Singapore, the United Kingdom, Canada, Australia and France are countries where the greatest percentage of organizations invested in bandwidth to enable the use of social media. (see Line Graph 4).
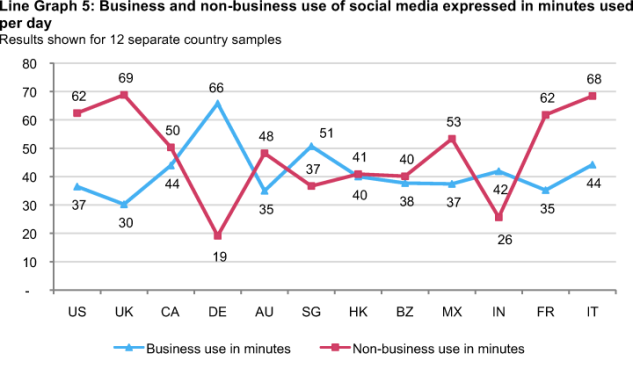
Use of social media for business and non-business purposes. According to Line Graph 5, organizations in Germany are more likely to have the highest use of social media for business purposes. Countries with the highest use of social media for non-business reasons are the United States, the United Kingdom, France, Italy, and Mexico. The countries with the fewest minutes used for personal reasons are Germany and India.
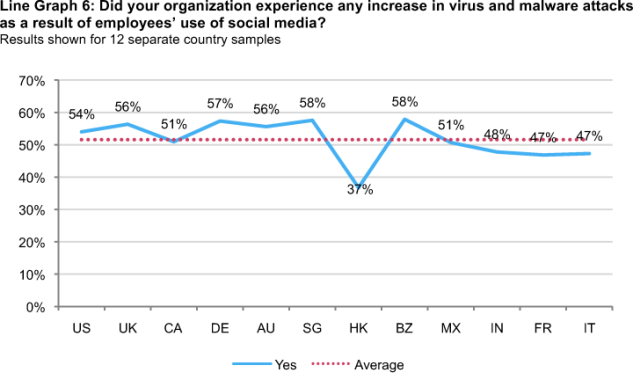
Virus and malware attacks as a result of social media usage. As shown in Line Graph 6, respondents in Hong Kong report the lowest level of increase in malware attacks as a result of employees’ use of social media. Singapore, Brazil and Germany report the highest increase in such attacks. Overall results clearly show that respondents in all countries believe their organizations suffered from an increase in malware activities as a result of social media used by employees in the workplace.
Part 4: Methods
Table 4 reports the sample response for 12 separate country samples. The sample response for this study was conducted over a 30-day period ending in July 2011. Our consolidated sampling frame of practitioners in 12 countries consisted of 116,491 individuals who have bona fide credentials in the IT or IT security fields. From this sampling frame, we captured 5,131 returns of which 491 were rejected for reliability issues. Our final consolidated sample before screening was 4,640, thus resulting in a 4.0 percent response rate.
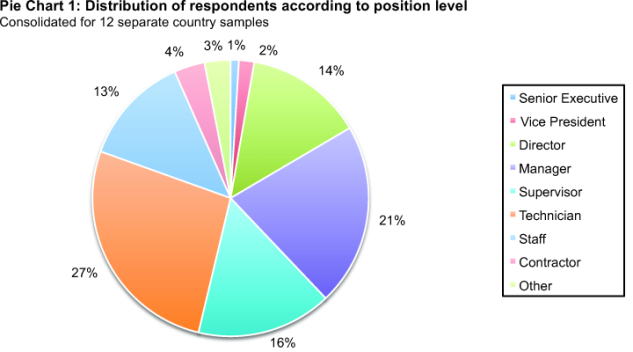
Pie Chart 1 summarizes the approximate position levels of respondents in our study. As can be seen, the majority (54 percent) of respondents are at or above the supervisory level. The respondents’ average experience in IT or IT security is 10.35 years.
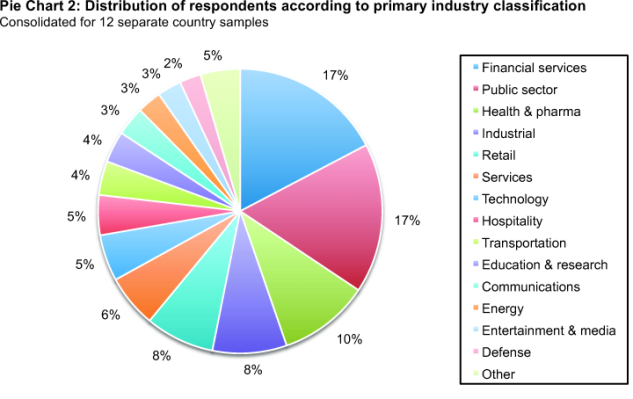
Pie Chart 2 reports on the respondent organizations’ primary industry segments. As shown, 17 percent of respondents are located in financial services, which includes banking, investment management, insurance, brokerage, payments and credit cards. Another 17 percent are located in public sector organizations, including central and local government.
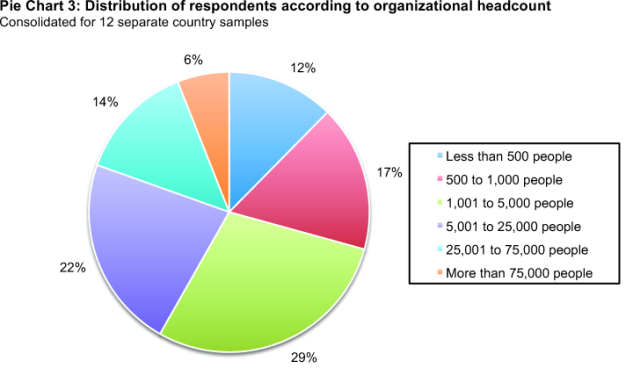
According to Pie Chart 3, the majority of respondents (71 percent) are located in larger-sized organizations with a global headcount of more than 1,000 employees.
Part 5: Recommendations & Caveats
In every part of the globe, IT and IT security practitioners recognize the positive impact social media is having on their organizations’ ability to market and communicate effectively. The challenge they face is how to ensure that the use of social media vehicles does not jeopardize the security of their organizations’ networks. We believe that specific steps can be taken to reduce the risk without hindering the opportunities social media offers. To achieve the right balance between enabling the use of social media and protecting the organization’s network from attacks, we have the following recommendations:
- Understand the risk social media tools create in the workplace. Conduct a risk assessment to understand what practices may be putting the organization at risk.
- Educate employees about how their social media usage could impact the company, such as how posting something inappropriate could breach company security and hurt its reputation.
- Create a comprehensive policy (including detailed guidelines) for all employees and contractors who use social media tools in the workplace. The policy should address the risks and the security procedures that should be followed.
- Improve the ability to detect and prevent attacks through expertise and enabling technologies.
- Consider the use of time quotas, bandwidth management and coaching to allow employees the freedom of the social web with policy controls to keep productivity and resource utilization in check.
Limitations
There are inherent limitations to survey research that need to be carefully considered before drawing inferences from findings. The following items are specific limitations that are germane to most web-based surveys.
- Non-response bias: The current findings are based on a sample of survey returns. We sent surveys to a representative sample of IT and IT security practitioners in 12 countries, resulting in a large number of usable returned responses. Despite non-response tests, it is always possible that individuals who did not participate are substantially different in terms of underlying beliefs from those who completed the survey.
- Sampling-frame bias: The accuracy is based on contact information and the degree to which the list is representative of individuals who are IT or IT security practitioners who deal with network or security issues. We also acknowledge that responses from paper, interviews or telephone might result in a different pattern of findings.
- Self-reported results: The quality of survey research is based on the integrity of confidential responses received from respondents. While certain checks and balances were incorporated into our survey evaluation process, there is always the possibility that certain respondents did not provide responses that reflect their true opinions.
Appendix: Audited Findings
The following tables report the percentage frequencies for all survey questions relating to social media in the workplace (Part 1). The consolidated values for 12 separate country samples are reported. See Table 1 for additional details. Please note that Part 2 of the survey instrument is not reported here. These additional survey questions pertain to the use of mobile devices in the workplace and will be presented in a future report. All survey responses were gathered in July 2011.
Part 1. Social media
Part 3. Organizational characteristics & respondent demographics
Learn more about Bloomberg Law or Log In to keep reading:
See Breaking News in Context
Bloomberg Law provides trusted coverage of current events enhanced with legal analysis.
Already a subscriber?
Log in to keep reading or access research tools and resources.