Introduction
The focus of this research—by Ponemon Institute and sponsored by Kingston—is to better understand how complex business and government organizations manage the security and privacy requirements of data collected and retained on USB drives.
We believe the lesson to be learned from the research is that organizations do understand they are at risk because of employees’ negligence but are not taking the necessary steps to secure USB drives. The main reasons cited for not being proactive include: uncertainty about monitoring and tracking USB use in the workplace, desire not to diminish productivity and the reliance on employee integrity and trustworthiness.
Our study also reveals that while these devices may be small, the data breaches that can result from lost or stolen USBs are huge. More than 70 percent of respondents in this study say that they are absolutely certain (47 percent) or believe that it was most likely (23 percent) that a data breach was caused by sensitive or confidential information contained on a missing USB drive. On average organizations in our study have lost more than 12,000 records about customers, consumers and employees as a result of missing USBs.
The following are ten USB security practices that many or most organizations in our study do not practice:
- Providing employees with approved, quality USB drives for use in the workplace.
- Creating policies and training programs that define acceptable and unacceptable uses of USB drives.
- Making sure employees who have access to sensitive and confidential data only use secure USB drives.
- Determining USB drive reliability and integrity before purchasing by confirming compliance with leading security standards and ensuring that there is no malicious code on these tools.
- Deploying encryption for data stored on the USB drive.
- Monitoring and tracking USB drives as part of asset management procedures.
- Scanning devices for virus or malware infections.
- Using passwords or locks.
- Encrypting sensitive data on USB drives.
- Having procedures in place to recover lost USB drives.
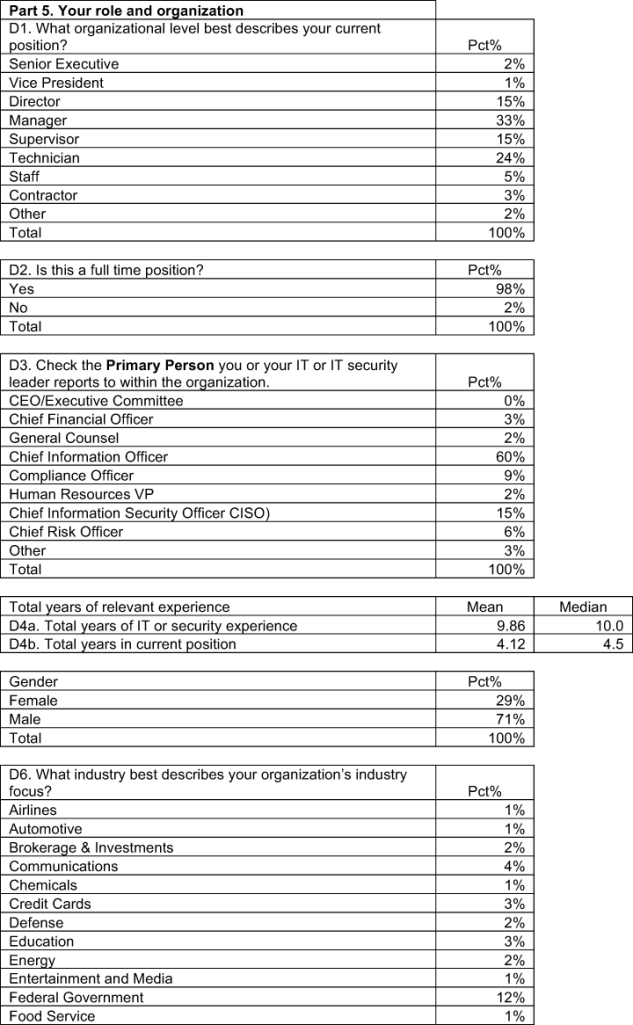
We surveyed 743 IT and IT security practitioners with an average of ten years of relevant experience. Most of the respondents report through the IT organization (CIO) or to the organization’s information security leader. The majority of respondents acknowledge the importance of USB drive security in meeting data protection and business objectives.
The next section reports the key findings of our independently conducted survey research. Taken together, our results provide strong evidence that organizations are not addressing the potential data protection and security risks caused by the rash of ubiquitous and unsafe USB drives that pervade many organizations.
Part 2. Key Findings
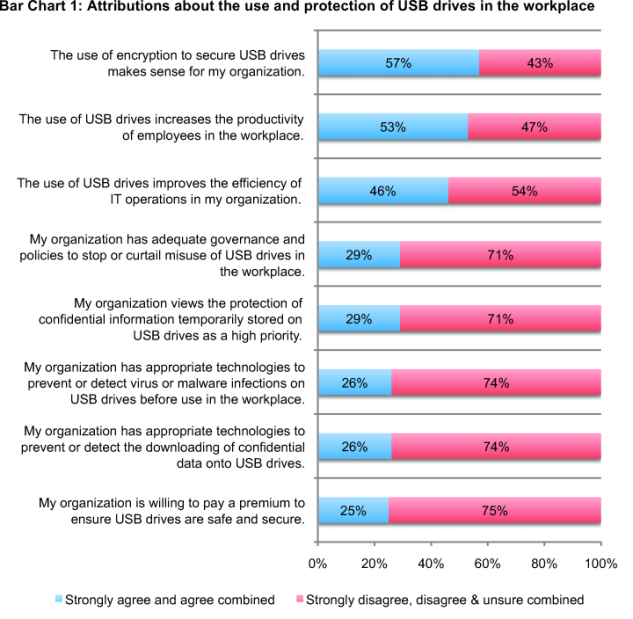
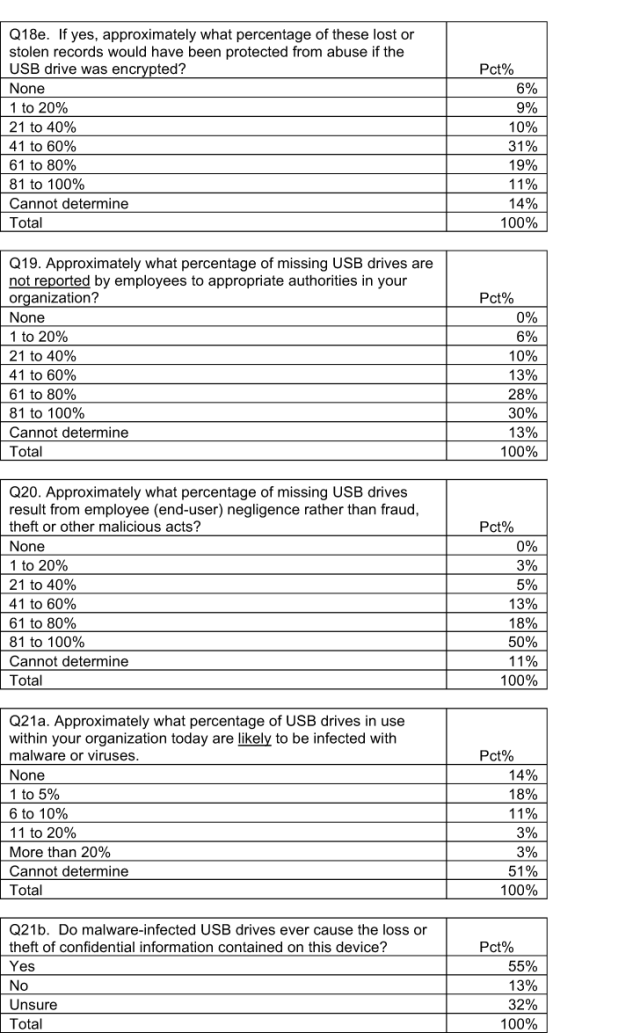
Organizations are ignoring the risk of unencrypted USB drives. Bar Chart 1 reports eight statements about the use and security of USB drives in respondents’ organizations. Each statement or “attribution” is rated by respondents using a five-point scale from strongly agree to strongly disagree. To simplify results, we consolidate responses into two groups—namely favorable (strongly agree and agree responses) and unfavorable (strongly disagree, disagree and unsure responses).
Seventy-one percent of respondents do not believe that their organizations consider the protection of confidential and sensitive information collected and temporarily stored on USB drives as a high priority. This is evidenced by the belief of 74 percent of respondents who say their organizations do not have the appropriate technologies to prevent or quickly detect the downloading of confidential data onto USB drives by unauthorized parties. The same percentage also say their organization does not have appropriate technologies to prevent or quickly detect virus or malware infections that may reside on USB drives before use by employees in the workplace.
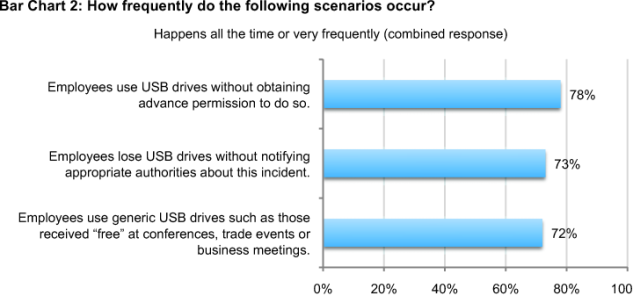
Employees are negligent when using USB drives and this is putting organizations’ sensitive data at risk. Employees are doing the following: using USB drives without obtaining advance permission to do so all the time (50 percent) and frequently (28 percent); losing USB drives without notifying appropriate authorities about this incident all the time (49 percent) or very frequent (24 percent); and using generic USB drives such as those received free at conferences, trade events and business meetings all the time (52 percent) and frequently (20 percent).
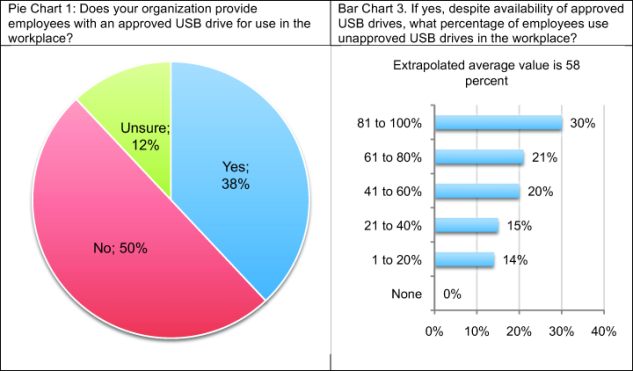
Despite awareness of employees’ abuse of USB drives, the vast majority of respondents (75 percent) say their organizations are not willing to pay a premium to ensure USB drives used by employees are safe and secure (not shown in the chart). In fact, as presented in Pie Chart 1, half of respondents say their organizations do not provide employees with approved USB drives and 12 percent are unsure. While 38 percent of respondents’ organizations supposedly provide approved USB drives to employees, an extrapolated average of 58 percent of employees in these organizations continue to use unapproved USB drives (see Bar Chart 3).
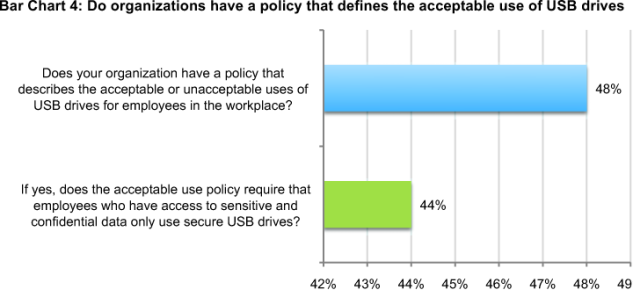
Organizations could improve the state of USB security by having policies that define the acceptable use of USB drives and enforcing those policies. As shown in Bar Chart 4, fewer than half (48 percent) of respondents say their organizations have USB security policies that define acceptable use.
Of those organizations that have policies, 44 percent say they require employees who have access to sensitive and confidential data to only use company-approved or secure USB drives. While not shown in the chart, 39 percent say their organizations do not require this and 17 percent are unsure.
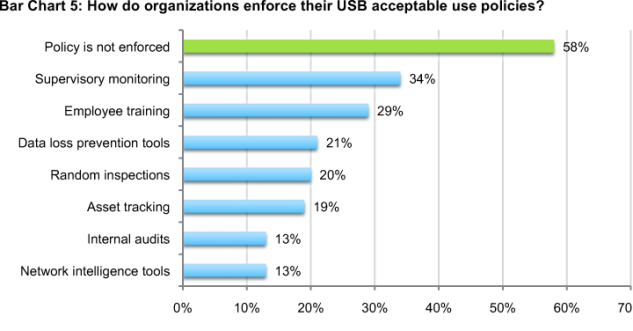
Bar Chart 5 summarizes how compliance is enforced. In many cases, acceptable use policies are really meaningless because 58 percent say they do not enforce compliance followed by 34 percent who say they enforce compliance through supervisory monitoring and 29 percent who say they enforce compliance through employee training. The top two reasons for not enforcing these policies are that they do not have the tools or resources to monitor compliance and the desire not to hinder employee productivity.
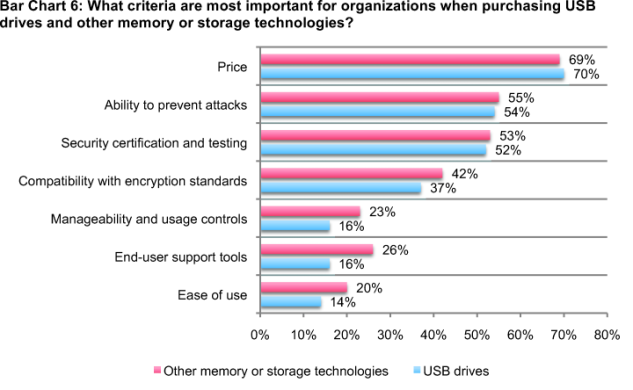
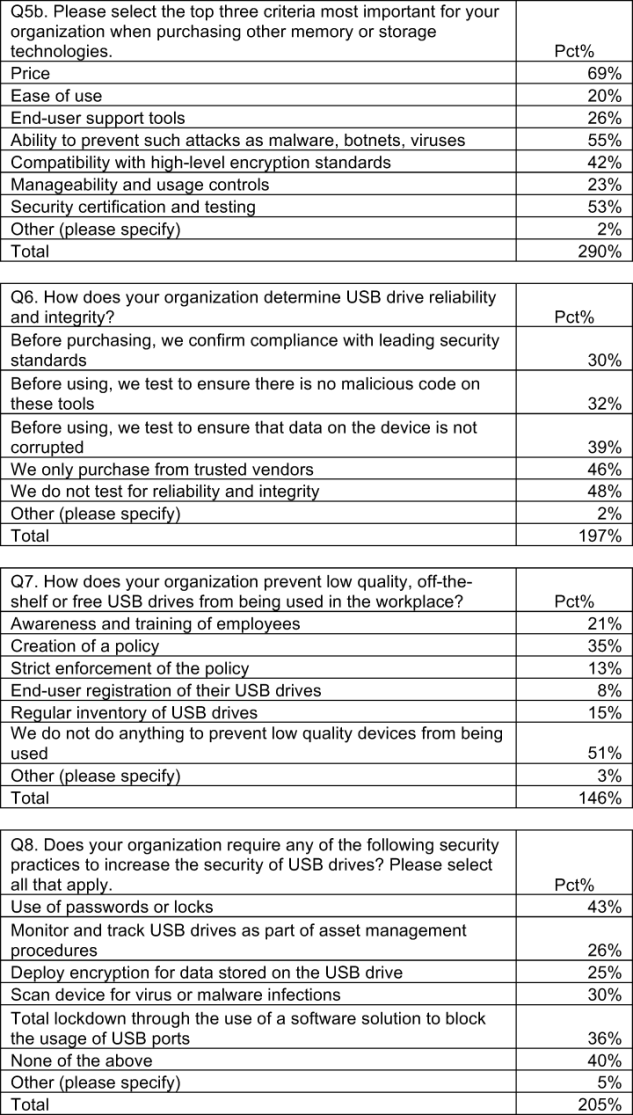
Organizations use the same criteria for the selection of USBs as they do for other memory or storage technologies. This comparison is shown in Bar Chart 6. As reported, price; the ability to prevent malware, botnets and viruses; and security certification and testing are the top three criteria most important for the purchase of USB drives. Despite concern about not diminishing productivity, end-user support tools and ease of use are not as important for USB drives as for other memory or storage technologies.
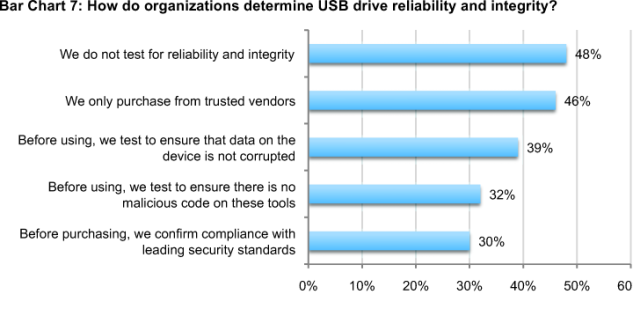
Bar Chart 7 shows how organizations attempt to vet USB reliability. According to 48 percent of respondents, organizations do not test for reliability and integrity in advance of use by employees. About one-third of respondents (32 percent) say their organizations test devices for malicious code. Thirty percent say they confirm USB drive compliance with leading security standards (such as the National Institute of Standards and Technology (NIST) Federal Information Processing Standard ( FIPS Pub. 140-2 ) before purchasing them.
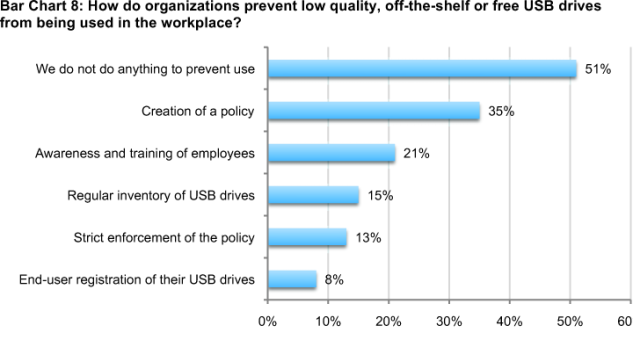
According to Bar Chart 8, to keep low quality USBs out of the hands of their employees, more than half (51 percent) of respondents say their organization does not do anything. Thirty-five percent say they have a policy and 21 percent they have awareness and training initiatives for their employees.
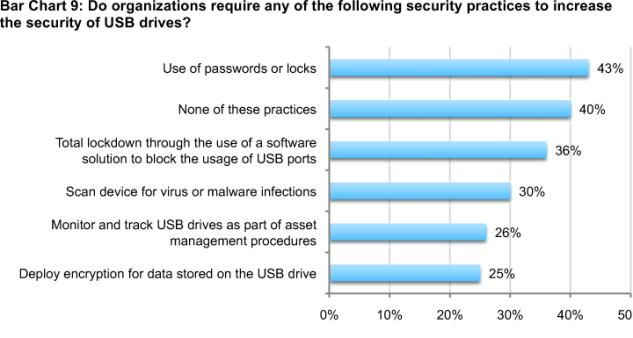
In addition, a large number of respondents say their organization is not required to adopt the following security practices to increase the security of USB drives: use passwords or locks, total lockdown through the use of a software solution to block the usage of USB ports, scan devices for virus or malware infections, monitor and track USB drives as part of asset management procedures, and deploy encryption for data stored on the USB drive.
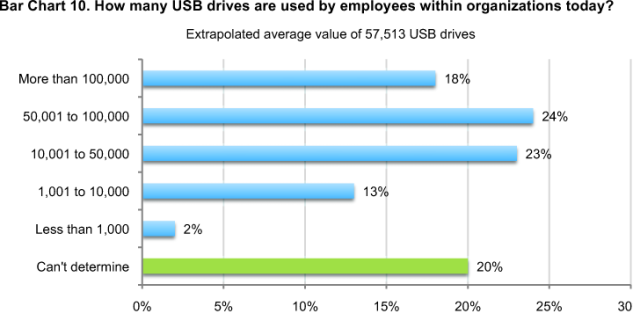
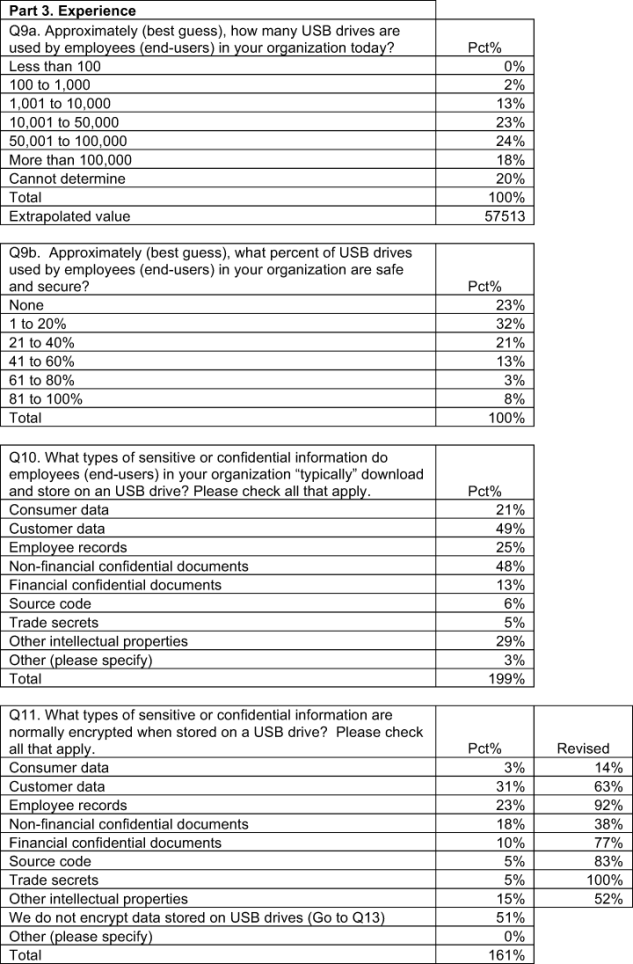
It is not surprising, based on the perceptions of respondents, that most employees’ USB devices are not secure and contain confidential business information. As reported in Bar Chart 10, on average, organizations in our study report the use of more than 57,000 USB drives. Approximately 75 percent of these are not considered secure. Typically, employees download customer data, non-financial confidential documents and other intellectual properties.
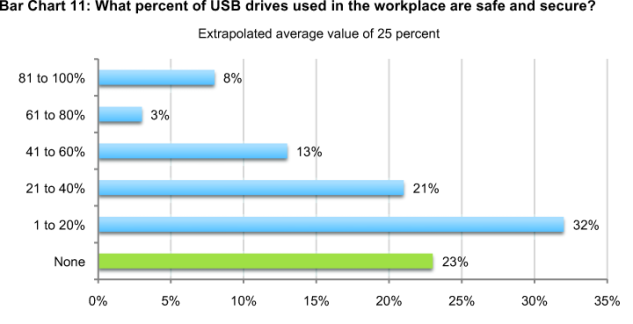
As shown in Bar Chart 11, on average 25 percent of USB drives used by employees are considered safe and secure according to respondents. The most at-risk information assets often temporarily stored on USB devices include customer data, non-financial confidential documents and other intellectual properties (including design documents and source code).
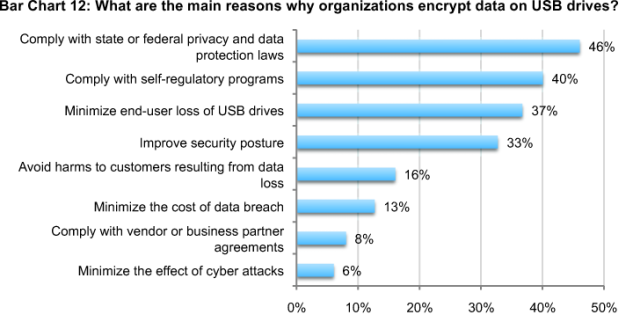
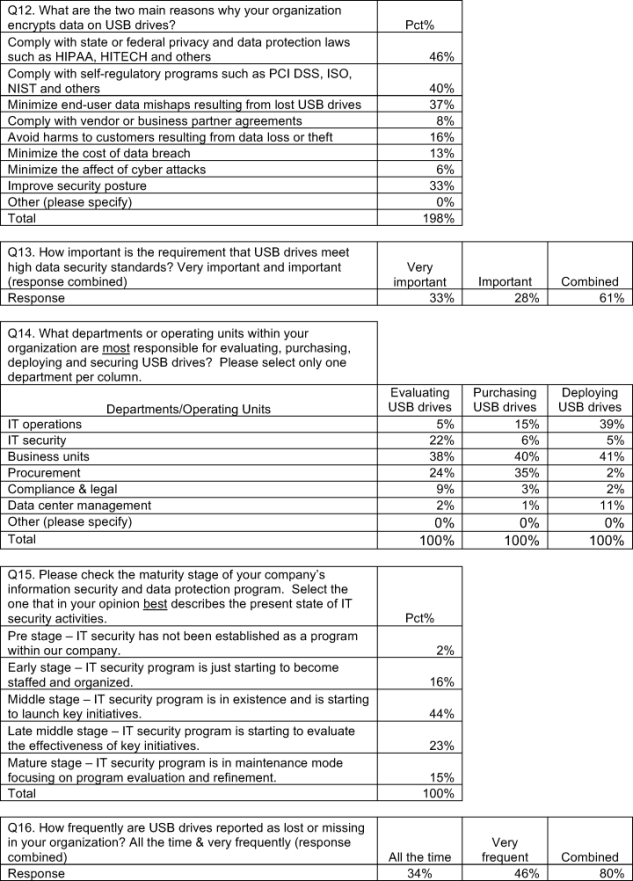
More than half (51 percent) of respondents report that they do not encrypt data stored on USB drives (not shown in the chart). If they do encrypt, it is to be in compliance with state or federal privacy and data protection laws and self-regulatory programs such as the Payment Card Industry Data Security Standard (PCI DSS), International Standards Organization (ISO), NIST and others. Bar Chart 12 summarizes other reasons organizations encrypt USB drives.
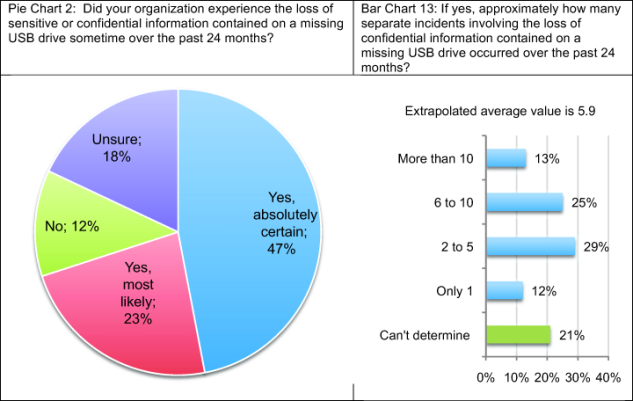
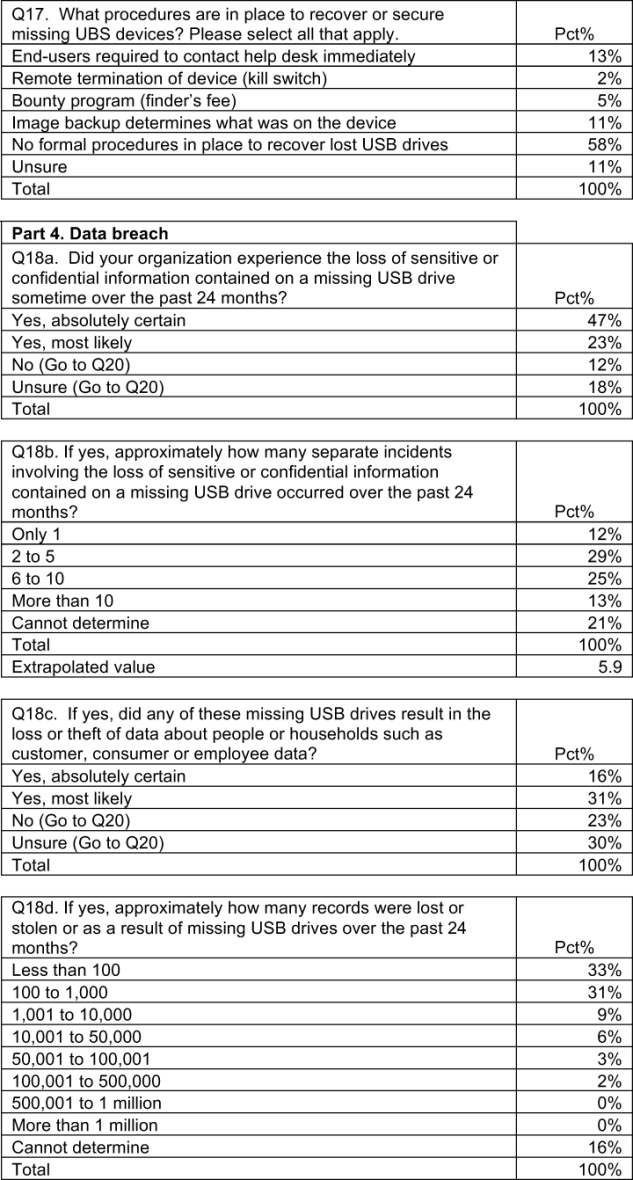
The devices may be small but the data breaches as a result of missing USBs can be devastating. Pie Chart 2 reveals that 47 percent of respondents say they are absolutely certain that their organization experienced the loss of sensitive or confidential information on a missing USB drive during the past two years. To make matters worse, respondents believe data loss or theft caused by insecure USB drives happen frequently—such as 5.9 times on average using extrapolation methods (see Bar Chart 13).
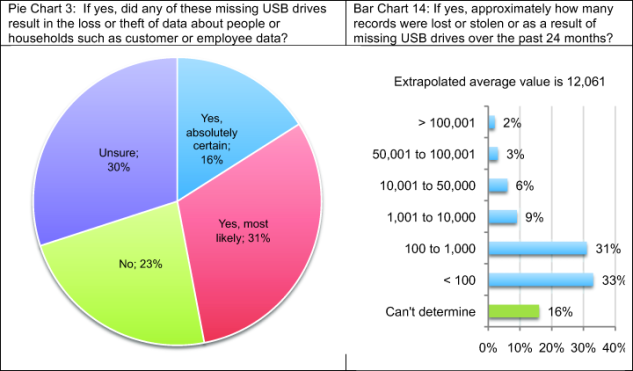
On average (see Bar Chart 14), respondents estimate that their organizations lost more than 12,000 records about customers, consumers and employees as the result of a lost or stolen USB drives over the past two years. Pie Chart 3 reveals that 40 percent of those respondents say that due to the loss of a USB drive, their organization had a data breach.
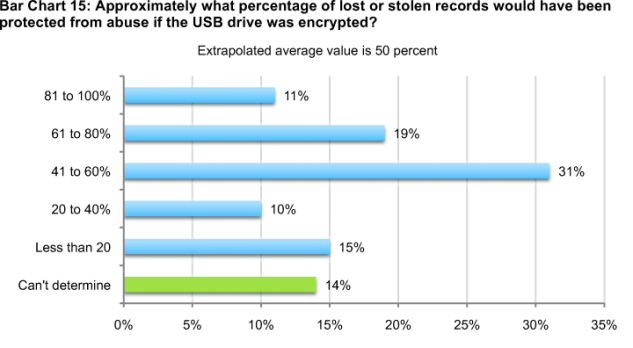
Respondents believe, on average, about half of all data lost or stolen from USB devices would be protected if the USB drive had been properly encrypted.
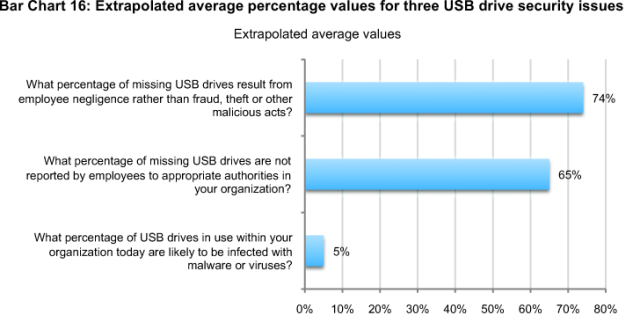
End-user negligence as opposed to maliciousness is most often the cause of missing USB drives. On average, 74 percent of missing USB drives for organizations in our study is caused by negligence. Based on this finding, training and awareness programs and policies should be the first steps organizations take to improve the state of USB security. In addition, 65 percent of respondents believe employees in the organizations will not report a lost USB drive to authorities. Finally, respondents believe on average only 5 percent of USB drives are likely to be infected with malware or viruses.
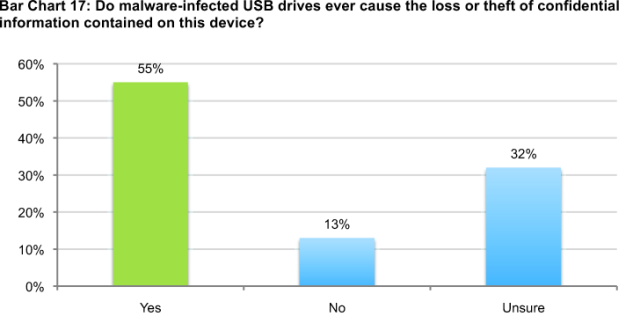
Despite the low infection rate mentioned above, as shown in Bar Chart 17, more than 55 percent of respondents believe malware-infected USB drives cause the loss of information assets contained on insecure USB drives.
Part 3. Methods
Table 1 summarizes the sample response for this study conducted over a five-day period ending in June 2011. Our sampling frame of practitioners consisted of 20,779 individuals located in the United States who have bona fide credentials in the IT or IT security fields. From this sampling frame, we invited 19,511 individuals. This resulted in 856 individuals completing the survey of which 113 were rejected for reliability issues. Our final sample was 743, resulting in a 3.6 percent response rate.
On average, respondents held 9.86 years of experience in either the IT or IT security fields. Twenty-nine percent of respondents are female and 71 percent male. Table 2 shows the organizational level of respondents. As shown, 51 percent of respondents are above the supervisory level.
Table 3 shows the headcount (size) of respondents’ business companies or government entities. As can be seen, 52 percent of respondents are employed by larger-sized organizations with more than 5,000 individuals.
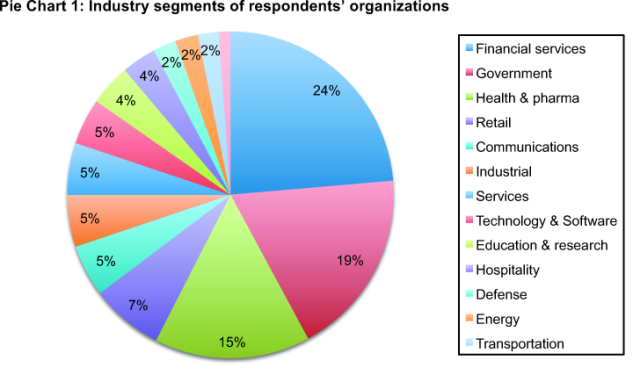
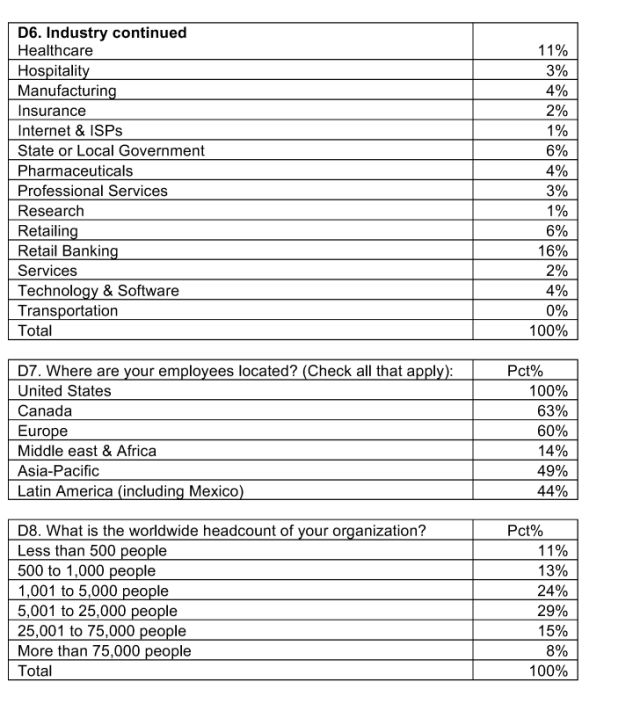
Pie Chart 1 shows the industry distribution for respondents who are employed by private and public sector organizations. As can be seen, the largest sectors include financial services (including banking, insurance, credit cards, investment management), public sector (including federal, state and local government organizations), and health care and pharmaceuticals.
Table 4 reports the geographic footprint of respondents’ organizations. In total, 74 percent of organizations have operations (headcount) in two or more countries. In addition, 60 percent have operations in one or more European nations. Finally, a total of 45 percent have operations in all major regions of the world.
Part 4. Conclusion
USB drives have become an indispensable technology for employees in all organizations. However, as shown in this study, lost or stolen USB drives pose great risks to an organization’s most sensitive and confidential information. While organizations seem to understand the need to become more proactive in making sure employees are not negligent, USB security practices do not seem to be a part of their overall data protection strategy.
In our introduction to this report, we listed ten USB security practices that many or most organizations participating in this study do not practice. Reasons for not doing so include uncertainty about how to go about monitoring and tracking their use in the workplace, a desire not to diminish employees’ productivity, and a hope and belief that employees will do the right thing and immediately report if they have lost a USB drive with sensitive information.
Our goal in presenting this research is to show that USBs may look insignificant but the consequences of a data breach from a lost or stolen device can be huge. More than 70 percent of respondents in this study say they are absolutely certain or believe it was most likely that their organizations experienced a data breach as the result of sensitive or confidential information contained on a missing USB drive. On average, organizations in our study have lost more than 12,000 records about customers, consumers and employees contained on USB drives. Based on Ponemon Institute’s 2010 Annual Cost of a Data Breach, the financial consequences of losing 12,000 records can cost an organization as much as $2.6 million.
Caveats
There are inherent limitations to survey research that need to be carefully considered before drawing inferences from findings. The following items are specific limitations that are germane to most web-based surveys.
- Non-response bias: The current findings are based on a sample of survey returns. We sent surveys to a representative sample of IT and IT security practitioners, resulting in a large number of usable returned responses. Despite non-response tests, it is always possible that individuals who did not participate are substantially different in terms of underlying beliefs from those who completed the survey.
- Sampling-frame bias: The accuracy is based on contact information and the degree to which the list is representative of individuals who are IT or IT security practitioners who deal with data protection or information security issues. We also acknowledge that responses from paper, interviews or telephone might result in a different pattern of findings.
- Self-reported results: The quality of survey research is based on the integrity of confidential responses received from respondents. While certain checks and balances were incorporated into our survey evaluation process, there is always the possibility that certain respondents did not provide responses that reflect their true opinions.
Learn more about Bloomberg Law or Log In to keep reading:
See Breaking News in Context
Bloomberg Law provides trusted coverage of current events enhanced with legal analysis.
Already a subscriber?
Log in to keep reading or access research tools and resources.