Part 1: Introduction
Ponemon Institute is pleased to present the results of The Security of Cloud Infrastructure. This research was conducted to determine how organizations manage the inherent data security risks associated with information technology infrastructure services provided by public or hybrid cloud providers. Our study surveyed IT operations, IT security and compliance practitioners. The findings reveal the gulf between those working in IT and those in compliance about service provider controls, top security measures and roles and responsibilities.
Sponsored by Vormetric, the study’s goal is to learn how organizations resolve (or fail to resolve) the tradeoff between cloud efficiencies and IT security. The tension in cloud deployment seems to revolve around the assumption that cloud services are less secure than on-premise computing but the benefits seem to be perceived as outweighing the risks to sensitive and confidential data. This tension is especially acute for cloud infrastructure services. This is the fourth study conducted by Ponemon Institute on security and governance issues in cloud infrastructure services.
The study surveyed 613 IT and IT security practitioners and 405 individuals who work in compliance, privacy, data protection and other related fields in the United States. The total sample size is 1,018. Respondents were asked to self-report if they are familiar with cloud computing and if their organizations use cloud computing services. Only those individuals who are familiar with cloud computing were included in this sample.
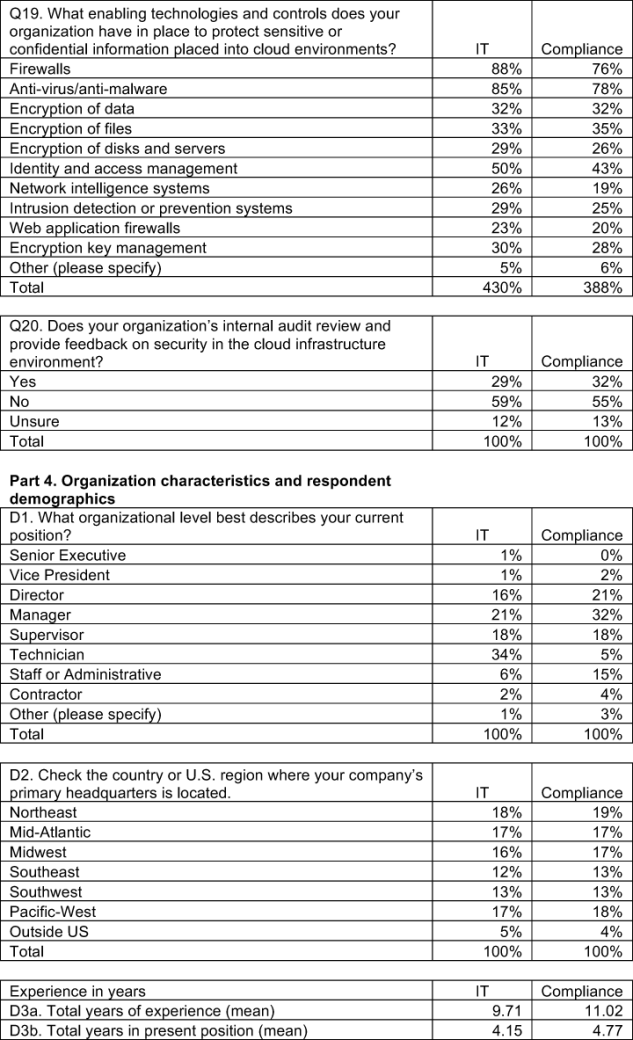
IT & IT security respondents (hereafter referred to as IT practitioners) have an average of approximately 10 years of experience in their field and the respondents in compliance have an average of 11 years of experience. More than half (57 percent) of the IT practitioners and 73 percent of the compliance respondents are at the supervisor or higher level. Seventy percent of IT and 66 percent of compliance practitioners work in organizations with a headcount of more than 2,000 employees.
We believe this study is important because it provides insights on how IT and compliance practitioners are at odds on some issues involving data security in the cloud. The following are the main differences:
- Only one-third of IT security respondents think IaaS environments are as secure as on premise data centers. However, half of compliance respondents think IaaS is as secure.
- A higher percentage (42 percent) of compliance respondents believe their organizations have adequate technologies to secure their IaaS environments. Only 35 percent of IT respondents think this is the case.
- IT respondents believe encryption should be used to make data unreadable by cloud services providers. However, compliance practitioners believe encryption should be used to enforce separation of duties that prevent IT administrators from accessing data they do not need in order to perform their work.
- Twenty-one percent of compliance officers say they are responsible for defining security requirements in the cloud and 22 percent of IT respondents believe business unit leaders are responsible for defining security requirements in the cloud. However, both groups agree that business unit leaders are responsible for enforcing cloud security requirements and no one role is responsible for implementing security in the cloud.
Other salient findings from this study are:
- The budget for cloud computing is increasing. On average, approximately 20 percent of the IT budget in organizations participating in this study is allocated to cloud services. However, this is expected to increase to approximately 31 percent over the next 12 to 24 months.
- Security concerns do not seem to prevent moving to the cloud. More than half (56 percent) of IT practitioners say that security concerns will not keep their organizations from adopting cloud services.
- Data in the IaaS [infrastructure as a service] cloud environment is perceived to be as a greater security risk. SaaS [software as a service] is considered by both groups to be more secure.
- Unstructured data is considered most important to store in the cloud infrastructure environment. Such data includes files, documents and e-mails.
- Internal audit is not included in cloud security issues. More than half of respondents say their organization’s internal audit review does not provide feedback about the security in cloud infrastructure.
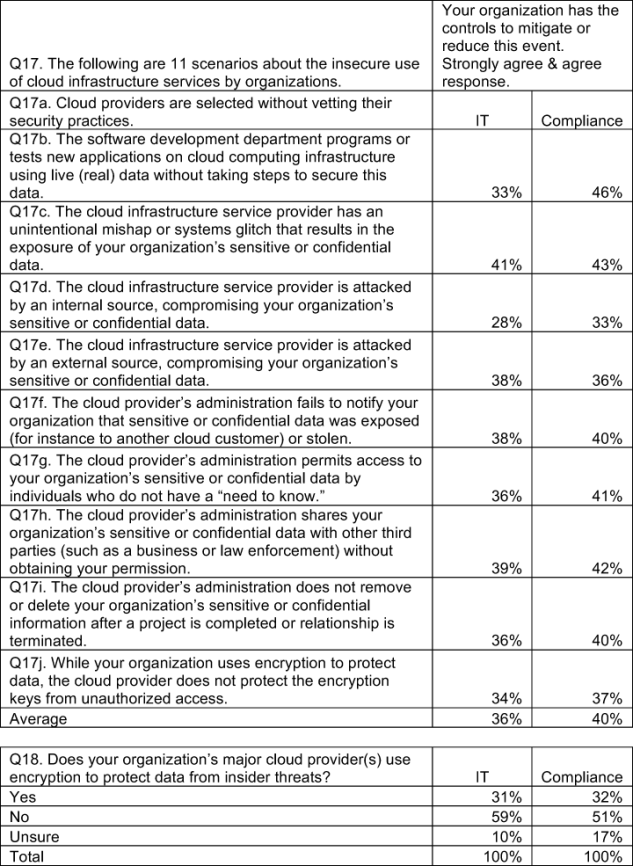
- Encryption is not widely used by cloud providers. Only 31 percent say their organization’s major cloud provider(s) use encryption to protect data from insider threats.
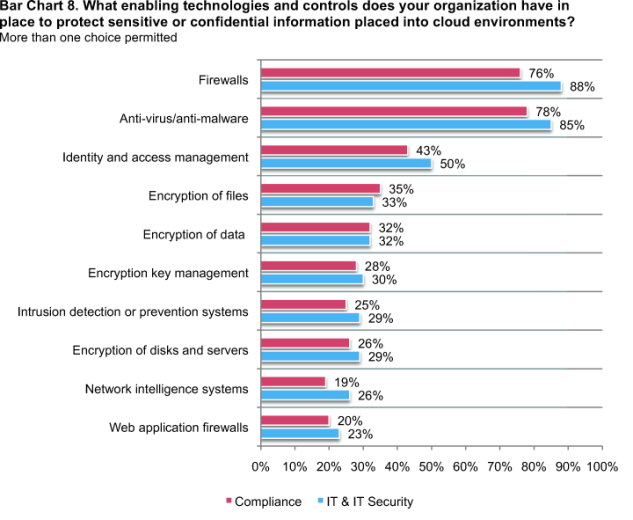
- Majority of organizations in our study use similar enabling technologies. Firewalls, anti-virus/anti-malware and identity and access management are the technologies and controls organizations have in place to protect sensitive or confidential information placed into cloud environments.
Part 2. Key Findings
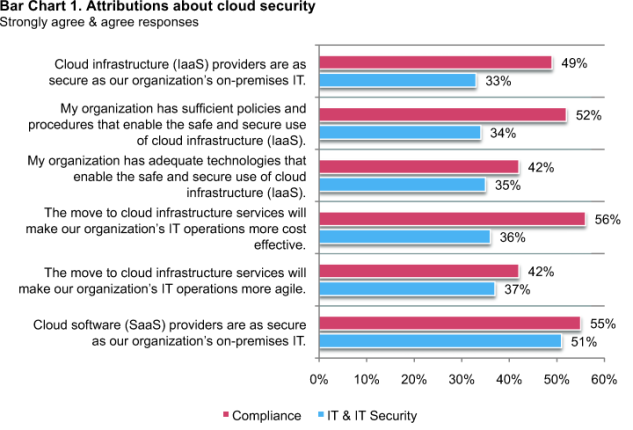
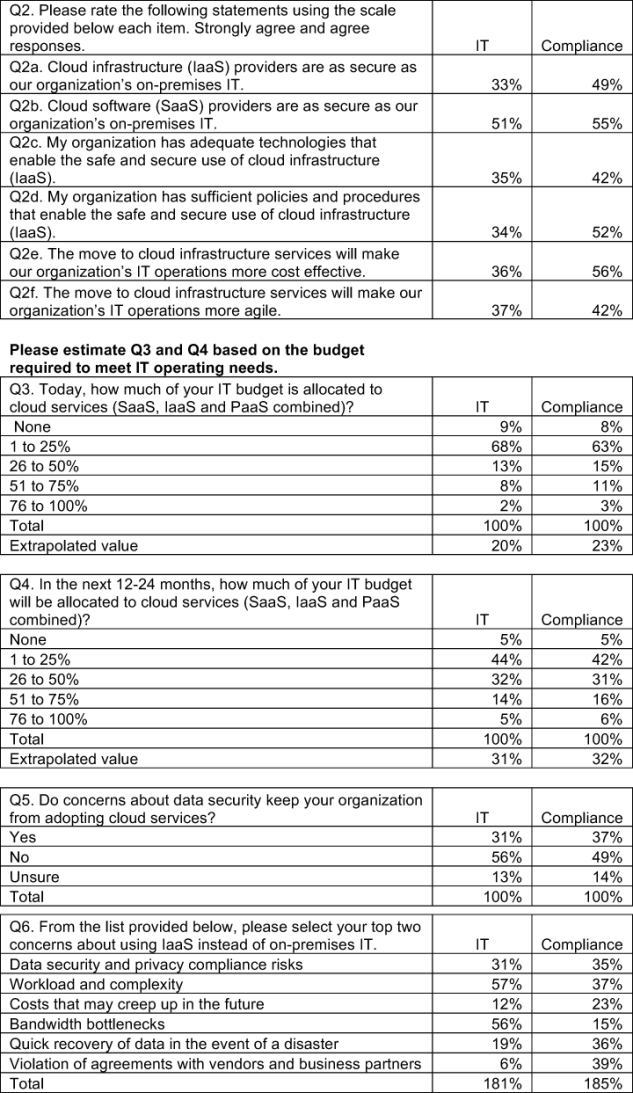
IT respondents are more concerned about security in the cloud than compliance respondents. Bar Chart 1 summarizes the strongly agree and agree response to six attributions concerning cloud security.
There is also a significant difference in agreement between IT and compliance respondents with respect to whether their organization has sufficient policies and procedures that enable the safe and secure use of cloud infrastructure (IaaS). Accordingly, only 34 percent of IT believe this is the case as opposed to 52 percent of the compliance respondents.
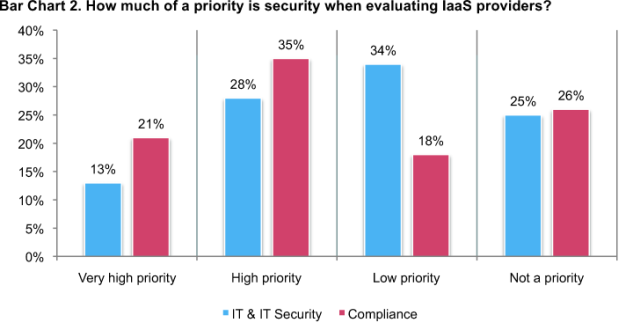
While there are concerns about security, the evaluation of the security of IaaS providers is rated as a low priority or not a priority. Bar Chart 2 shows 59 (34 + 25) percent of IT respondents say that when evaluating IaaS providers, security is a low or not a priority. In contrast, more than half of compliance respondents say security is a very high (21 percent) or high priority (35 percent) when evaluating IaaS providers.
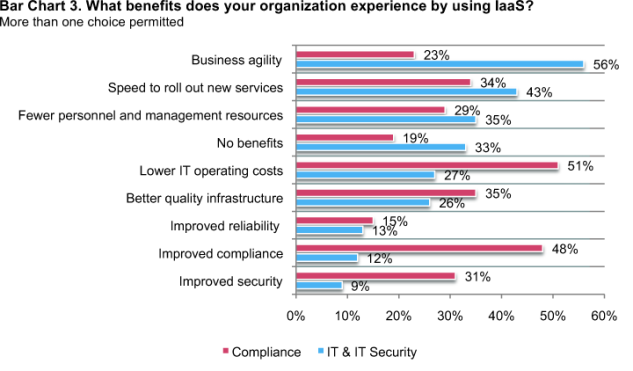
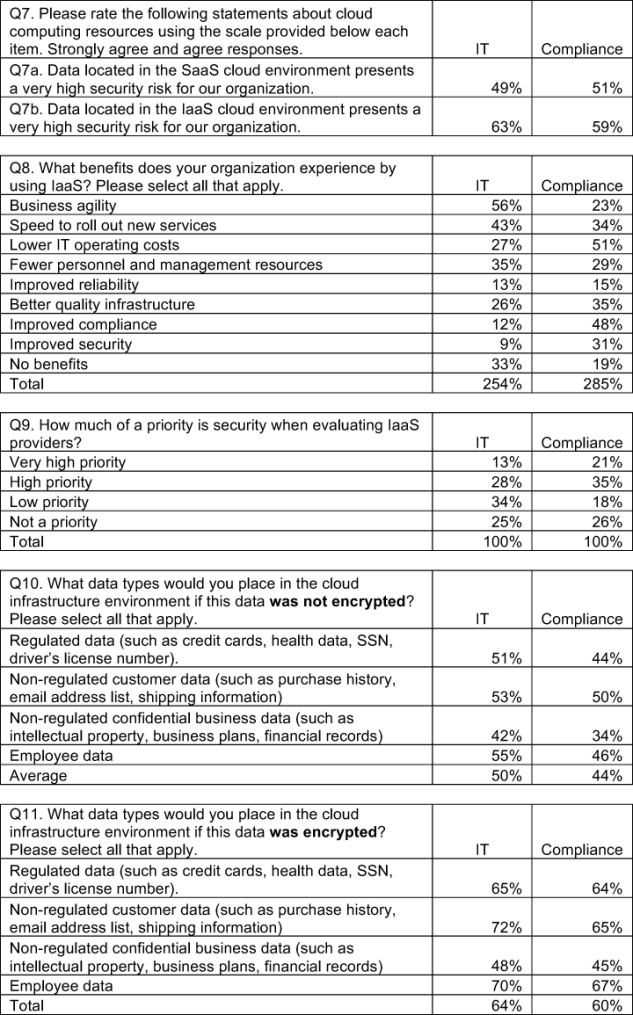
Bar Chart 3 reveals that these two groups see different benefits from using IaaS as opposed to on-premise IT resources. IT respondents believe business agility, speed to roll out new services and fewer personnel and management resources are the main benefits. Compliance respondents believe lower operating costs followed by improved compliance and better quality infrastructure are the main benefits. The widest gap or disagreement between these two samples concern improved compliance (Diff = 36 percent) and business agility (Diff = 33 percent).
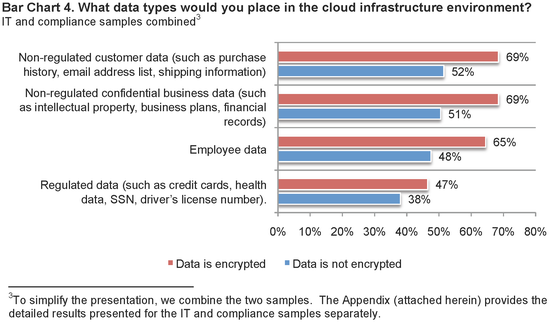
Encryption makes a difference when determining what data types to put in the cloud infrastructure. Bar Chart 4 presents respondents’ perceptions about four different data types that may be processed or retained in cloud environments. As can be seen, respondents (IT and compliance practitioners combined) say their organizations are more likely to place non-regulated customer data, non-regulated confidential business data, regulated data, and employee data in the cloud infrastructure environment if this data was encrypted.
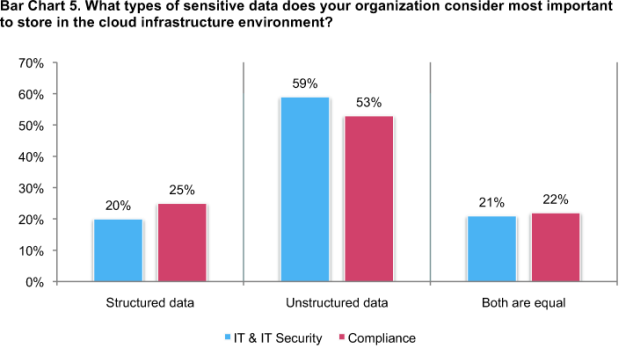
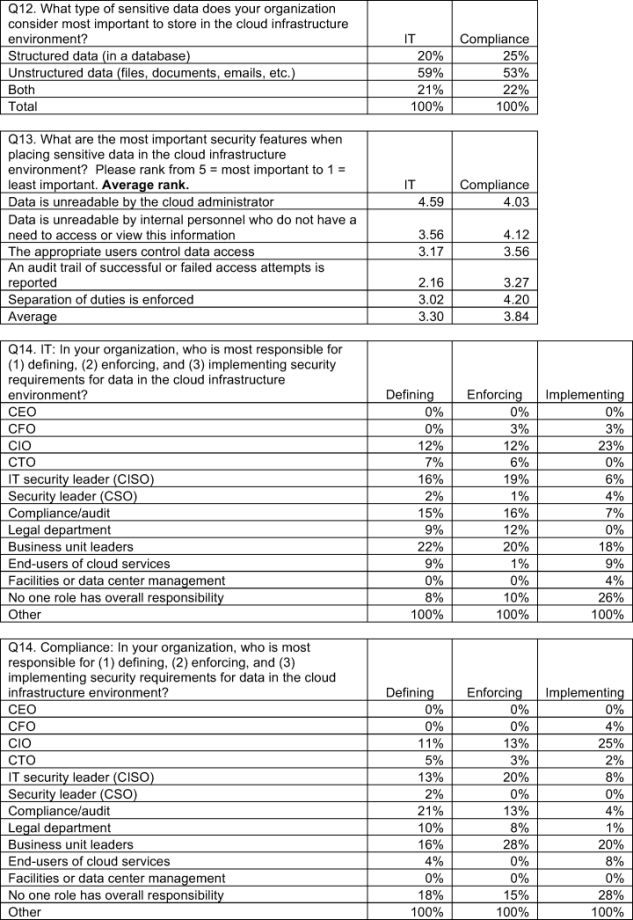
According to Bar Chart 5, a majority of IT (59 percent) and compliance (53 percent) respondents agree that unstructured data—such as e-mails, documents, spreadsheets and more—is the type of sensitive data organizations considered most important for storage in cloud infrastructure environments.
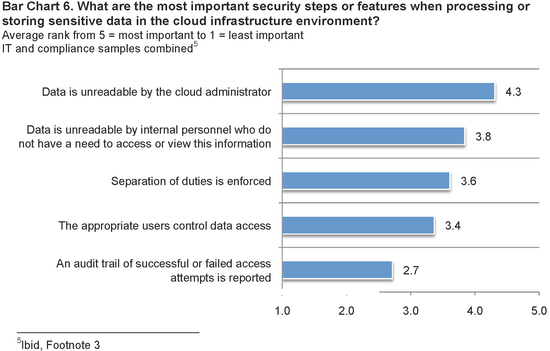
The security feature considered most important when placing sensitive data in the cloud infrastructure by both IT and compliance respondents is to make this data unreadable
to cloud administrators. Bar Chart 6 shows the average rank order of five security steps or features, wherein each feature is ranked from most important to least important. Clearly, the two top ranked security features concern making sensitive data unreadable to cloud administrators or other internal personnel who do not have a need to access or view this information.
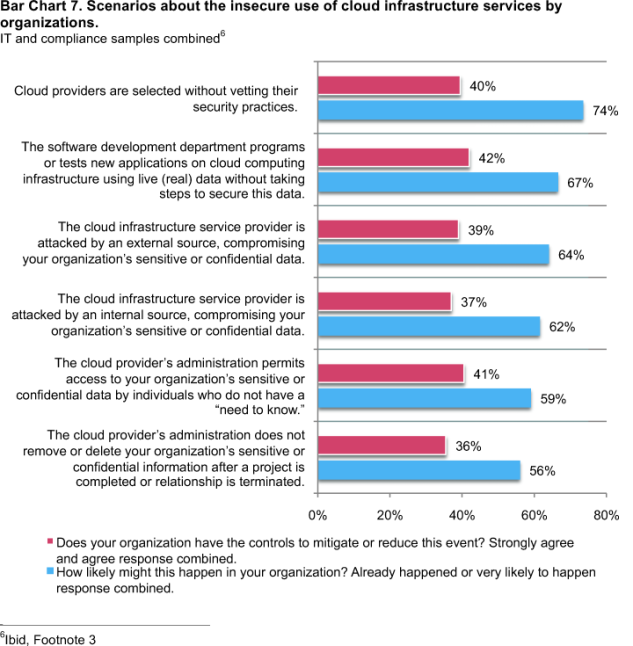
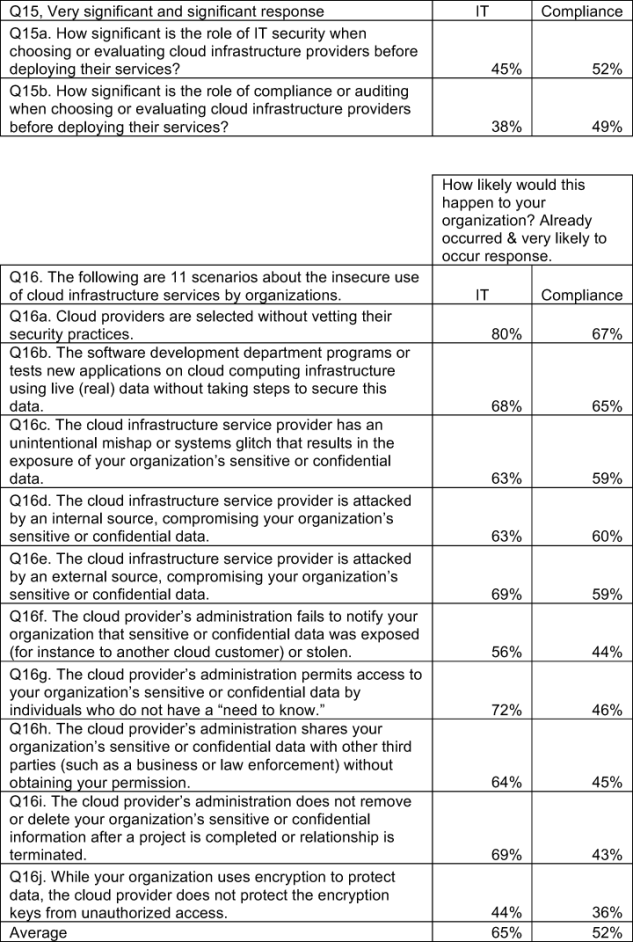
Organizations are at risk because of the lack of vetting and monitoring of IaaS providers. As summarized in Bar Chart 7, respondents (IT and compliance samples combined) believe their organizations are not proactive in ensuring the security of cloud providers. The majority of IT and compliance practitioners say that cloud providers have been selected or are very likely to be selected without vetting their security practices. Moreover, it appears that most organizations do not have the controls to mitigate or reduce the risk of these negative events.
According to respondents, cloud infrastructure security blunders already occurring or likely to occur include: software testing using live data without sufficient protections or controls (67 percent), the inability to curtail attacks from either external (64 percent) or internal (62 percent) sources, and the cloud administrator’s inability to control access to sensitive or confidential data (59 percent). According to 56 percent of respondents, another very likely cloud infrastructure vulnerability is not removing or deleting sensitive or confidential information after a project is completed or the relationship is terminated.
The above bar chart also reports the availability of controls to curtail or mitigate each stated cloud infrastructure vulnerability. As can be seen, a majority of respondents perceive a lack of controls that protect their organizations.
For instance, only 36 percent believe they have sufficient controls to ensure the removal or deletion of their organization’s information after a project is completed. Only 37 percent believe they have sufficient controls to protect the organization from malicious insiders and 39 percent say they have sufficient controls to defend against external attackers. Finally, only 41 percent believe they have sufficient controls to ensure cloud administrators restrict access on a “need to know” basis.
The majority of organizations use a similar set of enabling security technologies to protect sensitive or confidential data in the cloud infrastructure environment. Firewalls, anti-virus/anti-malware and identity and access management are the technologies and controls organizations have in place to protect sensitive or confidential data placed into cloud environments, as shown in Bar Chart 8, network intelligence systems and web application firewalls are the least used technologies to protect sensitive or confidential data placed in the cloud infrastructure environment.
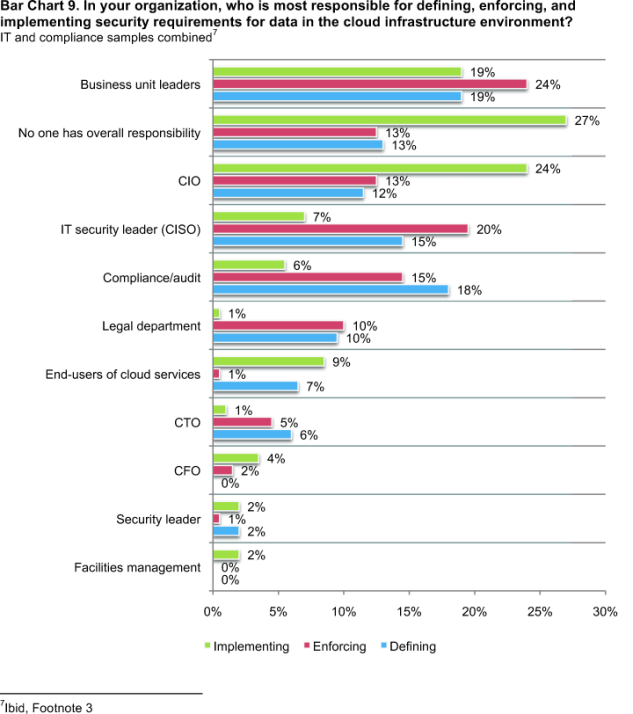
There is no clear function, department or individual responsible for defining, enforcing and implementing security requirements for data in the cloud infrastructure environment. According to Bar Chart 9, only 7 percent of respondents (IT and compliance samples combined) say the IT security leader or chief information security officer (CISO) is most responsible for implementing the organization’s cloud security requirements. Similarly, only 6 percent of respondents see the compliance/audit function as most responsible for implementing requirements. In contrast, 27 percent of respondents say no one person or function has overall responsibility for implementing cloud security requirements.
This bar chart also shows respondents generally agreeing that business unit leaders (24 percent), the CISO (20 percent) or the compliance/audit leader (15 percent) are most responsible for enforcing their organization’s cloud security requirements.
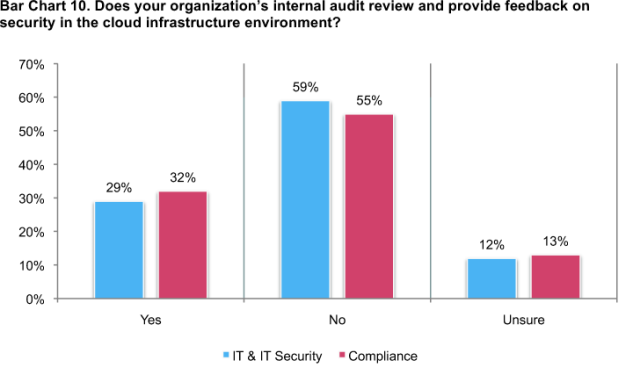
Internal auditors are not often called upon to review and provide feedback on security in the cloud. Bar Chart 10 reveals that a majority of respondents say their organizations do not use internal audits to review or provide feedback on the security of cloud infrastructure environments where sensitive or confidential information may be deployed.
Part 3. Methods
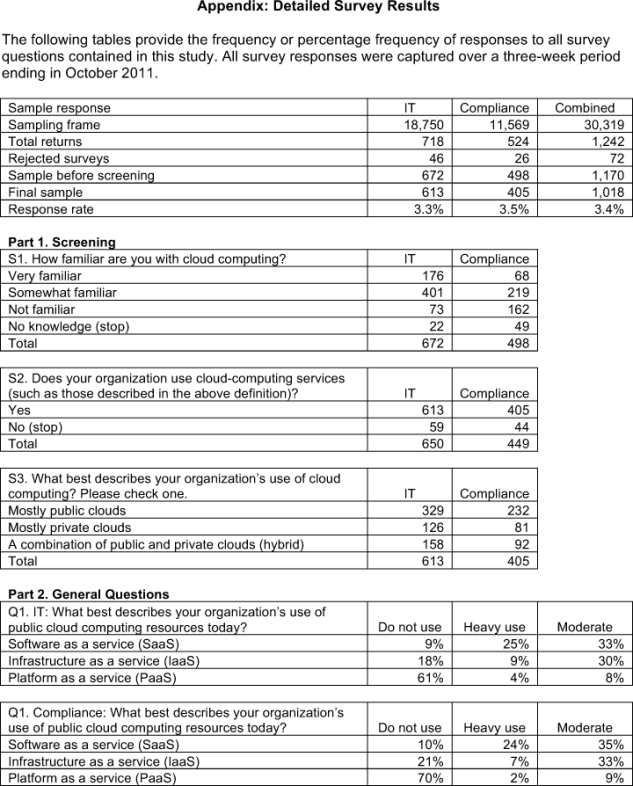
Table 1 summarizes the sampling response for a web-based survey we conducted over a three-week period concluding in October 2011. A total of 18,750 individuals in the IT and IT security fields as well as 11,569 individuals in various organizational compliance functions
Table 2 summarizes the organizational position of respondents in both the IT and IT security sample and compliance sample. As can be seen, respondents in both samples hold responsible positions. Fifty- seven percent of IT and IT security practitioners self-report they are at or above the supervisory level. Seventy-three percent of compliance practitioners say they are at or above the supervisory level.
As noted in Table 3, the average years of relevant work experience for IT and IT security practitioners is 9.7 years. The average years of relevant work experience for compliance practitioners is 11 years.
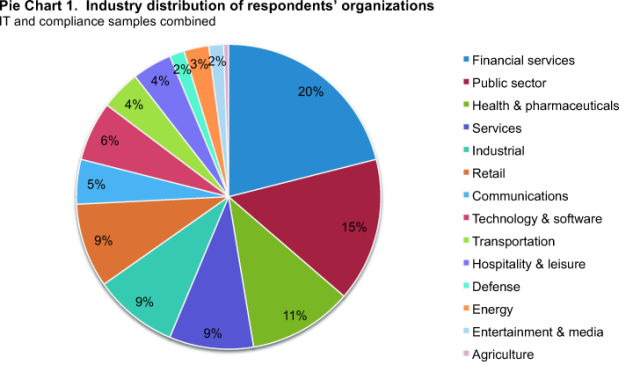
The industry classification of respondents’ organizations for both the IT and compliance samples (combined) is reported in Pie Chart 1. As can be seen, financial services represents the largest segment at 20 percent. The second largest segment is public sector at 15 percent. In addition, at 11 percent, the third largest segment concerns health and pharmaceutical companies.
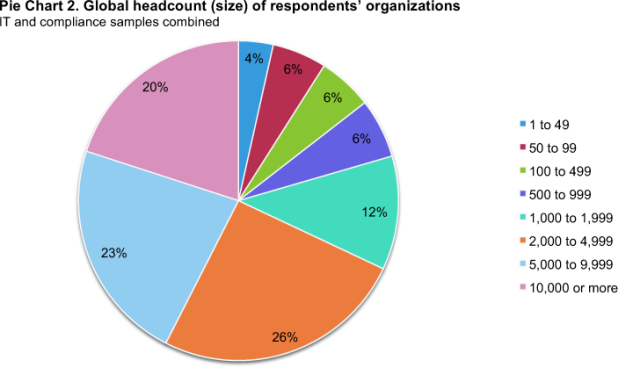
As shown in Pie Chart 2, approximately one-third (34 percent) of participating organizations have fewer than 1,000 employees. In contrast, 43 percent of the combined IT and compliance samples are represented by large organizations with 5,000 or more employees.
Part 4. Implications and limitations
The study reveals that in many cases, especially with IaaS, there is recognition that there are security risks to sensitive and confidential data stored in a cloud environment. However, the benefits and the desire to migrate to the cloud in organizations seem to outweigh the concerns.
We believe some of the main implications from this research are:
- Security in the cloud is a concern, especially in IaaS environments.
- Encryption is considered one of the most important enabling technologies for securing IaaS clouds.
- Organizations feel they lack adequate technologies to secure their IaaS environments.
- Ownership for security in the cloud is dispersed throughout the organization, making it difficult to implement an enterprise-wide data security strategy.
In summary, we believe this is the first study to survey both IT and compliance practitioners about the security of cloud infrastructure. Despite differences between the IT and compliance samples, we conclude that both groups are concerned about the security of sensitive or confidential data placed in the cloud infrastructure environment.
Caveats
There are inherent limitations to survey research that need to be carefully considered before drawing inferences from findings. The following items are specific limitations that are germane to most web-based surveys.
- Non-response bias: The current findings are based on a sample of survey returns. We sent surveys to a representative sample of individuals in IT and IT security located in the United States, resulting in a large number of usable returned responses. Despite non-response tests, it is always possible that individuals who did not participate are substantially different in terms of underlying beliefs or perceptions about data protection activities from those who completed the instrument.
- Sampling-frame bias: The accuracy is based on contact information and the degree to which the sample is representative of individuals in the IT, IT security and compliance fields. We also acknowledge that the results may be biased by external events.
- We also acknowledge bias caused by compensating respondents to complete this research within a holdout period. Finally, because we used a web-based collection method, it is possible that non-web responses by mailed survey or telephone call would result in a different pattern of findings.
- Self-reported results: The quality of survey research is based on the integrity of confidential responses received from subjects. While certain checks and balances can be incorporated into the survey process, there is always the possibility that certain respondents did not provide accurate responses.
Learn more about Bloomberg Law or Log In to keep reading:
See Breaking News in Context
Bloomberg Law provides trusted coverage of current events enhanced with legal analysis.
Already a subscriber?
Log in to keep reading or access research tools and resources.